This set of instructions will result in a PPTP server using local or RADIUS authentication on an Ubiquiti EdgeRouter. This assumes that you already have a basic working configuration already with a dynamic address assigned on the WAN interface and that there are some free IP addresses on the local network to assign to VPN clients.
GUI setup
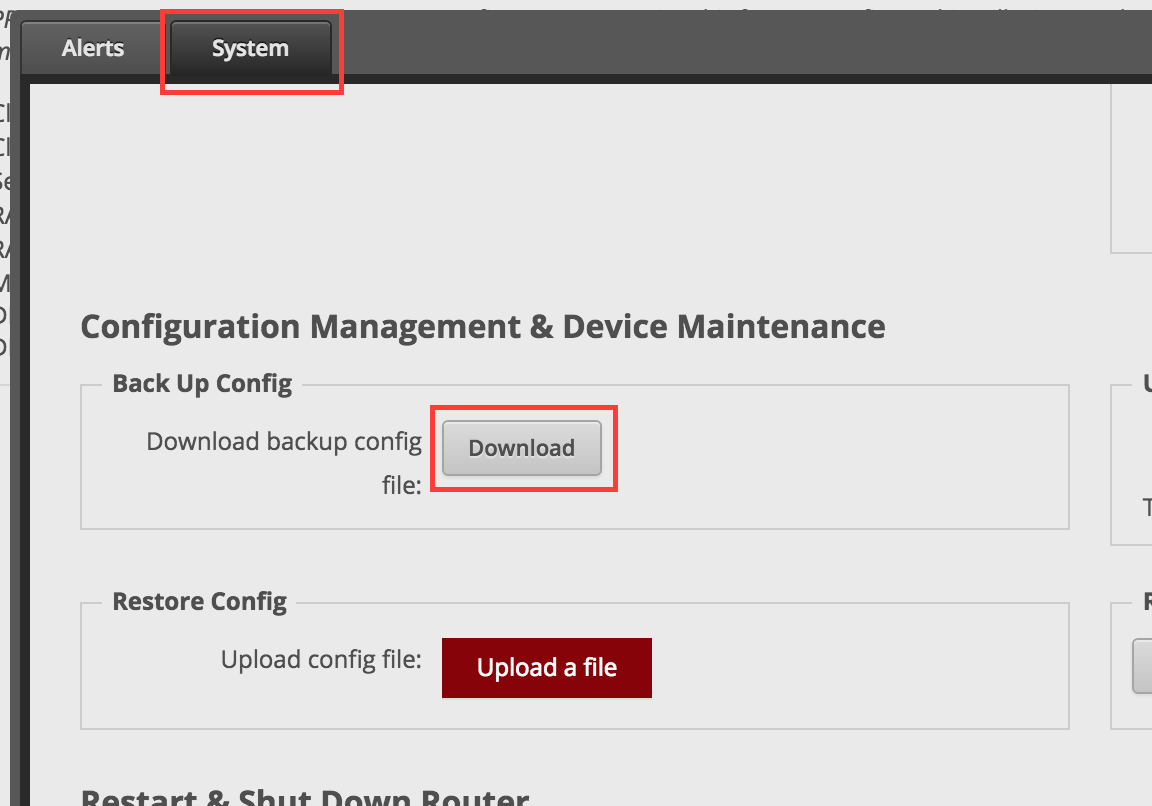
Backup configuration
Before changing any settings it’s usually a good idea to backup the router configuration. The router configuration file can be downloaded in the System tab on the bottom of the UI.
Firewall
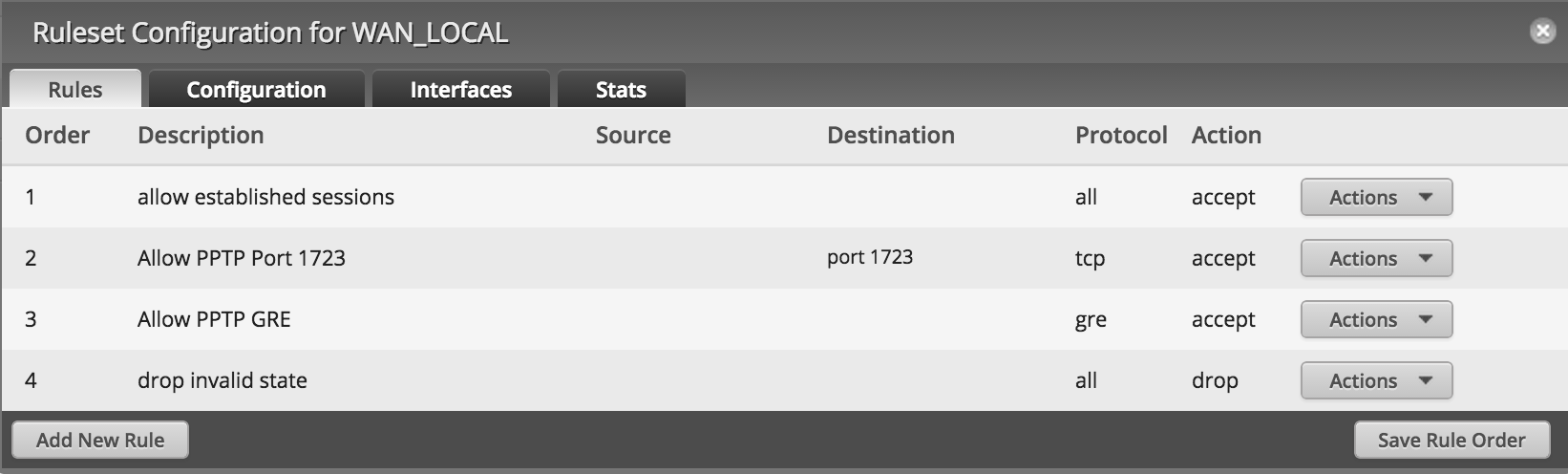
The following changes should be made in the WAN_LOCAL rule set (or whatever the rule that controls access to the router is called). They should be added before the invalid packets are dropped in the rule set.
PPTP: TCP port 1723
- Navigate to Firewall/NAT > Firewall Policies
- Click on Actions > Edit Ruleset next to the WAN_LOCAL ruleset
- Click Add New Rule
- Configure the new rule as shown
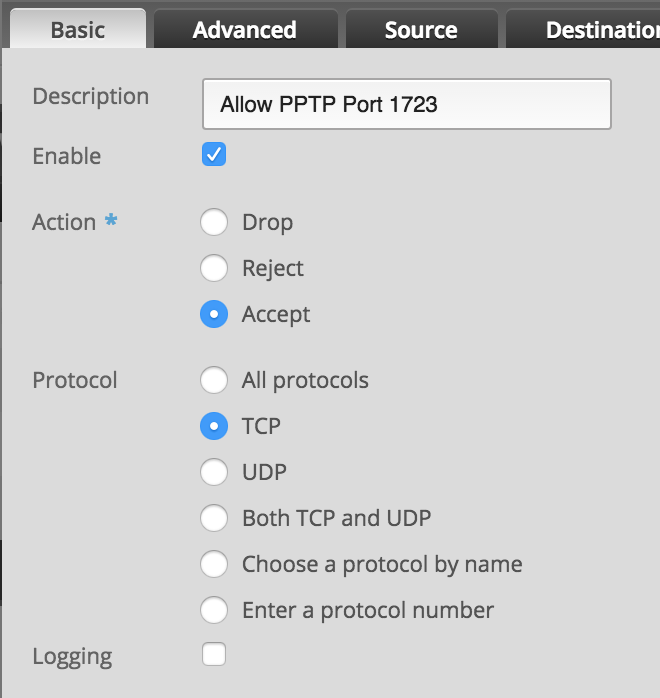
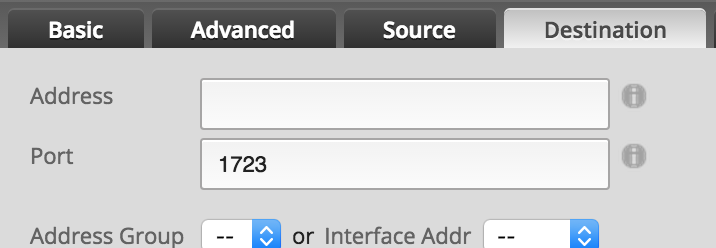
- Click Save
GRE: protocol 47
- Below the new rule and still above the rule to drop invalid packets, add another rule by clicking on Add New Rule
- Configure the rule as shown
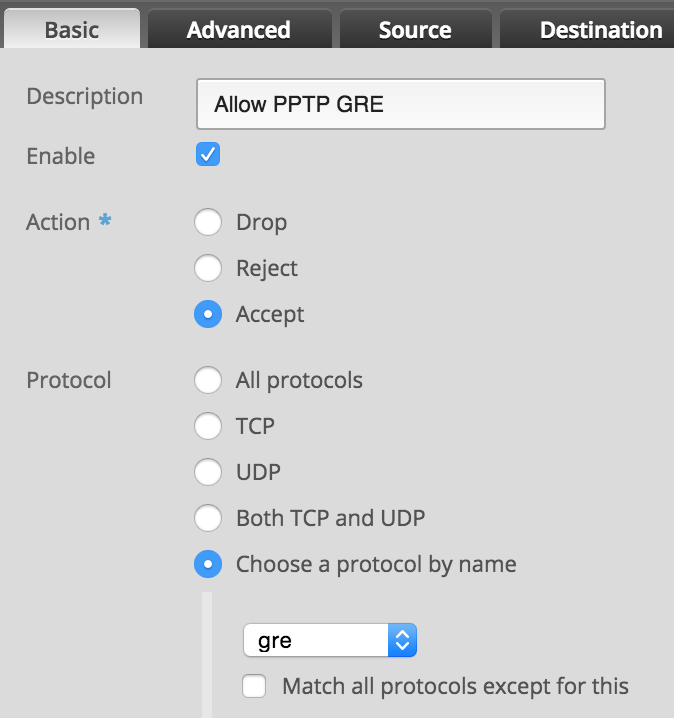
- Click Save
Ensure the rules look similar to what’s shown below, clicking and dragging them as necessary. After changing the order (if needed), click on Save Rule Order.
CLI setup
In order to make configuration changes, first SSH into the router (or login to the CLI through the GUI) and type
configure
at the terminal.
Authentication Mode
Local Authentication
set vpn pptp remote-access authentication mode local
For each user account that you’d like to be able to log in, use the following command to specify the username (foo in this example) and password (bar in this example) for each.
set vpn pptp remote-access authentication local-users username foo password bar
RADIUS Authentication
set vpn pptp remote-access authentication mode local
The IP address (192.168.1.50 in this example) and key (baz) for the RADIUS server can specified as follows.
set vpn pptp remote-access authentication radius-server 192.168.1.50 key baz
Pool Address
To specify the range of IP addresses for the VPN server to assign to clients
set vpn pptp remote-access client-ip-pool start 192.168.1.100 set vpn pptp remote-access client-ip-pool stop 192.168.1.150
Name Server
Specify the DNS servers for clients to use as follows; 8.8.8.8 and 8.8.4.4 are the public DNS servers for Google. I tried setting the DNS server to the router’s IP address, but that didn’t work on its own (though it might with additional configuration changes).
set vpn pptp remote-access dns-servers server-1 8.8.8.8
set vpn pptp remote-access dns-servers server-2 8.8.4.4
Commit, review, and save
Commit configuration changes using
commit
To review the PPTP remote access configuration
show vpn pptp remote-access
Finally, save the changes using
save
And typing
exit
will exit out of configure mode
References
- https://wiki.ubnt.com/PPTP_Remote_Access_-_CLI_Commands
- http://community.ubnt.com/t5/EdgeMAX/GUIDE-How-to-configure-Local-PPTP-VPN-on-1-5-0-Firmware-works-on/m-p/971155#U971155
- https://developers.google.com/speed/public-dns/

